King-phisher 1.5.1 with SSH keys + TLS
With version 1.5.1, we’ve seen a few slight changes to the setup process. Unlike previous tutorials, I’m not going to yabber on as we walk through the setup. If you want background details, reasoning behind choices made or any verbose info on any part of this setup, check out the earlier tutorial. This setup (similar to previous ones) will comprise of the king-phisher server sitting on a Digital Ocean Ubuntu 16.04.1 x64 box and a king-phisher client on a Kali 2016.2 rolling x64 box.
I’m personally using SSH keys (no password auth on the king-phisher server) on a non-standard port and it works seamlessly with king-phisher. Obviously you don’t have to, but just know that you can.
We will be using the Phishing_Awareness_v2 training package provided by SecureState for the web and email templates. Installation is now super smooth, with no dependency issues like matplotlib on the client that we’ve sometimes seen in previous versions. From start to finish, it should take less than 10 minutes.
Prerequisites
- A domain must be registered and an A record set for the server IP address in order to successfully generate a SSL certificate
- TCP ports 22, 80 and 443 must not be blocked by firewalls or in use by other processes on the king-phisher server
Note that when you generate your Lets Encrypt certificate, an apache2 process is started and hogs port 80 from that point forward until killed (which is why we manually smack it after our cert is generated). Default error verbosity is pretty good, and usually points clearly to the issue being experienced. 99% of the time it will be a process that’s already using a port required or a bad username/password.
King-phisher server setup
sysadmin@st0rm:~$ cd /opt && sudo git clone https://github.com/securestate/king-phisher.git
Cloning into 'king-phisher'...
remote: Counting objects: 12117, done.
...
...
Checking connectivity... done.
sysadmin@st0rm:/opt$ sudo king-phisher/tools/install.sh
Linux version detected as Ubuntu
Install and use PostgreSQL? (Highly recommended and required for upgrading) [Y/n] y
Will install and configure PostgreSQL for the server
...
...
You can start the King Phisher client with the following command:
python3 /opt/king-phisher/KingPhisher
sysadmin@st0rm:/opt$ sudo service king-phisher stop
sysadmin@st0rm:/opt$ sudo git clone https://github.com/securestate/king-phisher-templates.git
Cloning into 'king-phisher-templates'...
...
...
Checking connectivity... done.
sysadmin@st0rm:/opt$ sudo apt-get -y install python-letsencrypt-apache
Reading package lists... Done
...
...
Processing triggers for ufw (0.35-0ubuntu2) ...
sysadmin@st0rm:/opt$ sudo letsencrypt --apache certonly
...
...
(Enter recovery email address of your choice)
(Enter your domain name either with or without host depending on your setup)
...
...
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at
/etc/letsencrypt/live//fullchain.pem. Your cert
will expire on 2017-02-22. To obtain a new version of the
certificate in the future, simply run Let's Encrypt again.
- If you like Let's Encrypt, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
sysadmin@st0rm:/opt$ sudo vi /opt/king-phisher/server_config.yml
(Modify the relevant values to match the below:)
server:
# Bind address information, multiple ports can be addresses:
- host: 0.0.0.0
port: 443
ssl: true
ssl_cert: /etc/letsencrypt/live//fullchain.pem
ssl_key: /etc/letsencrypt/live//privkey.pem
sysadmin@st0rm:/opt$ sudo service apache2 stop
sysadmin@st0rm:/opt$ sudo apt-get install mailutils postfix
Reading package lists... Done
...
...
(Choose Internet Site and enter domain name)
...
...
Processing triggers for ufw (0.35-0ubuntu2) ...
sysadmin@st0rm:/opt$ sudo bash
root@st0rm:/opt# echo “root @” > /etc/postfix/generic
root@st0rm:/opt# postmap /etc/postfix/generic
root@st0rm:/opt# exit
sysadmin@st0rm:/opt$ sudo vi /etc/postfix/main.cf
(Modify the relevant values to match the below:)
inet_interfaces = 127.0.0.1
smtp_generic_maps = hash:/etc/postfix/generic
sysadmin@st0rm:/opt$ sudo service postfix restart
sysadmin@st0rm:/opt$ sudo service king-phisher start
sysadmin@st0rm:/opt$ sudo ln -s /opt/king-phisher-templates/Website_Templates/Training/Phishing_Awareness_v2/www/* /var/www/
King-phisher client setup
sw1tch@shad0w:~$ cd /opt && sudo git clone https://github.com/securestate/king-phisher.git
Cloning into 'king-phisher'...
...
...
Resolving deltas: 100% (8825/8825), done.
sysadmin@st0rm:/opt$ sudo git clone https://github.com/securestate/king-phisher-templates.git
Cloning into 'king-phisher-templates'...
...
...
Checking connectivity... done.
sw1tch@shad0w:/opt$ sudo king-phisher/tools/install.sh −−skip−server
Linux version detected as Kali
Skipping installing King Phisher Server components
...
...
You can start the King Phisher client with the following command:
python3 /opt/king-phisher/KingPhisher
sw1tch@shad0w:/opt$ python3 /opt/king-phisher/KingPhisher
Set up a default campaign, then click Edit>Preferences. Under the SMTP tab, configure using the below as an example:
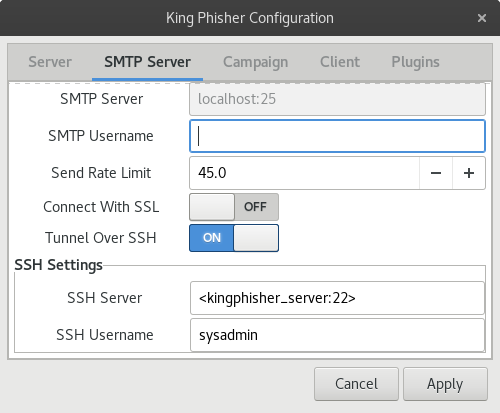
You should now have a functional king-phisher setup, ready for campaign configuration. For more detailed instructions on setting up campaigns and tweaking settings, check out the previous tutorial.
Thanks again @SecureState and especially @zeroSteiner for his awesome support.
